3 Ways SCIM 2.0 Simplifies User and Group Management in Tableau Cloud with Azure AD
Modern identity providers (IdPs) allow customers to manage user access across all of their cloud applications, including Tableau Cloud. By using an external IdP, Tableau Cloud customers can take advantage of automatic user provisioning in order to improve security and save time by centrally managing their users and groups.
Tableau Cloud supports automatic user provisioning with SCIM 2.0 for IdPs such as Okta, OneLogin, and Azure Active Directory (Azure AD).
Beginning with 2022.2, you can benefit from SCIM 2.0 support with Azure AD, the identity service provided by Microsoft. It’s one of the most popular IdPs used by Tableau Cloud customers. Here are three ways SCIM 2.0 simplifies user and group management in Tableau Cloud with Azure AD.
1. Provision users and groups automatically
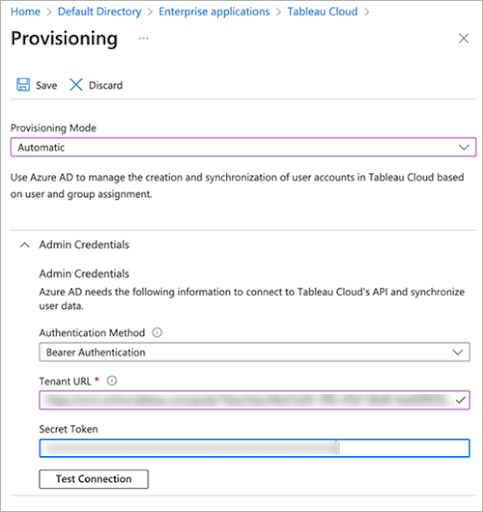
With Azure AD automatic provisioning, you can quickly synchronize your existing users and groups to Tableau Cloud and simplify the management of these resources.
When provisioning a user in Tableau Cloud, the site administrator can sync the user’s UPN, authentication method, site role, and group membership to Tableau Cloud. With automatic user provisioning, customers can manage their users and groups centrally in their IdP such as Azure AD. Tableau Cloud will then automatically stay in sync with the IdP, adding and removing users and groups based on the provisioning assignments configured in the IdP. This can improve security and significantly reduce the amount of manual work that Tableau Cloud site administrators need to do to manage site users and group membership.
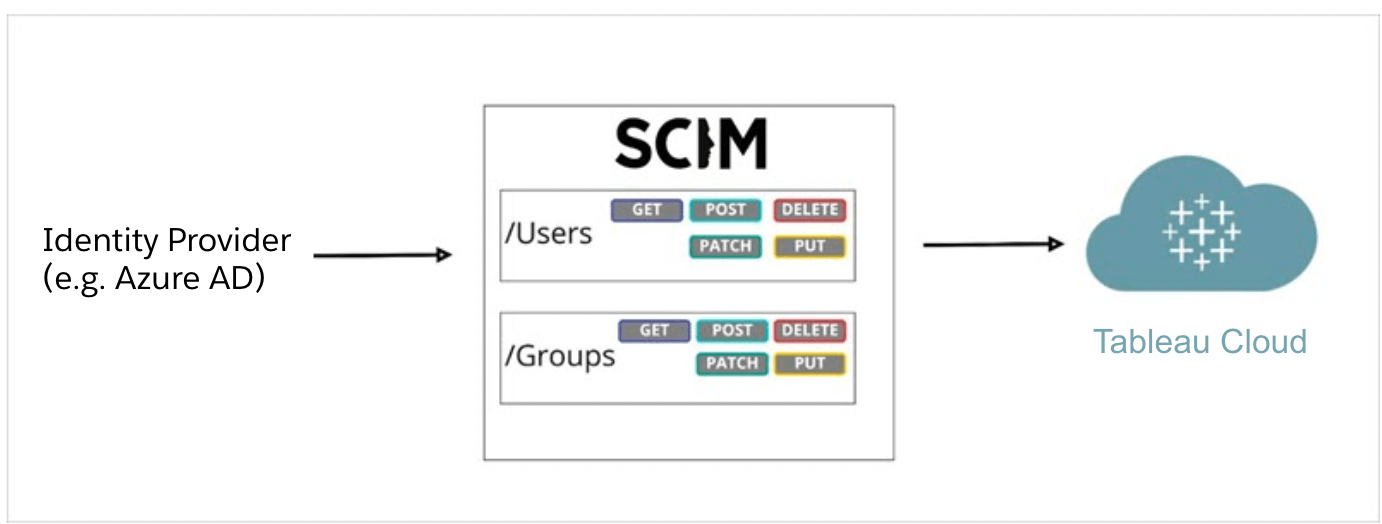
2. Secure provisioning requests with a bearer token
Previously, the Tableau Cloud and Azure AD integration supported a legacy method of authentication called basic authentication. However, with basic authentication, provisioning requests were through credentials such as username and password, which are no longer recommended through SCIM 2.0 industry standards.
With Azure AD SCIM 2.0 support, you can now take advantage of security tokens called bearer tokens when authenticating requests. The OAuth 2.0 bearer token is a cryptographic string that Azure AD sends in the authorization header when a user is attempting to sign into a Tableau Cloud site. One key benefit of using bearer tokens is that they are specific to the application and resources for which they are used (in this case a Tableau Cloud site), so they cannot be reused.
3. Support users that belong to multiple groups
Prior to SCIM 2.0 support with Azure, administrators leveraging Azure AD for provisioning to Tableau Cloud had to be mindful of the groups that users belonged to. When a user had multiple roles (grants) assigned directly or inherited from groups, it would cause an error. Administrators would need to ensure that a user only belonged to a single group, which was time-consuming for organizations with thousands of users and groups that needed to be provisioned.
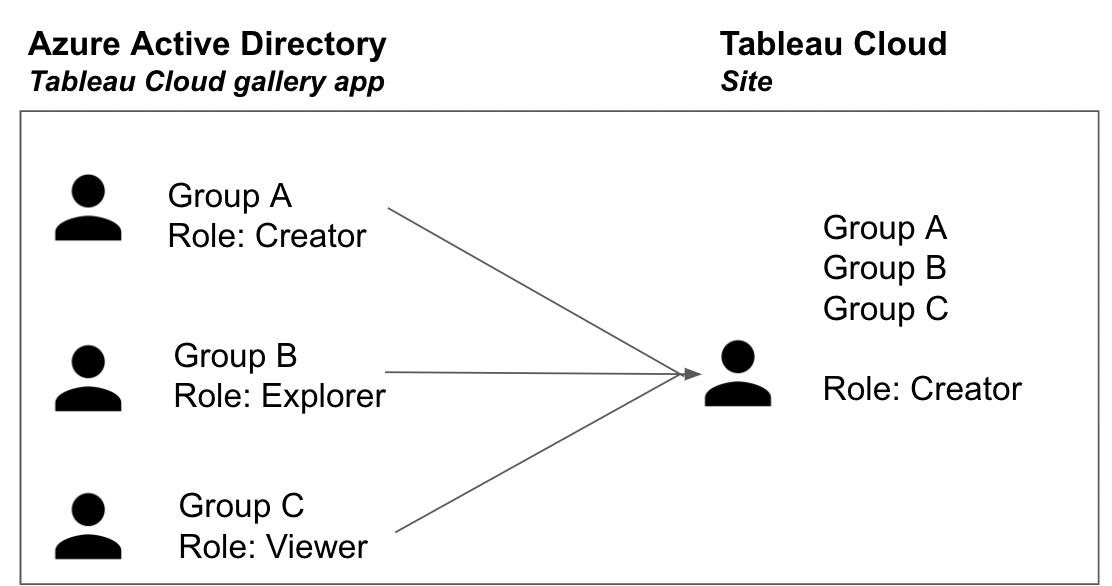
Now an administrator can provision groups to Tableau Cloud without cross-checking a user’s group membership. When a user belongs to multiple groups with varying levels of role assignments, the system will accept the user and grant them the most permissive role by default. The most permissive role will be the role that is saved for the user in Tableau Cloud.
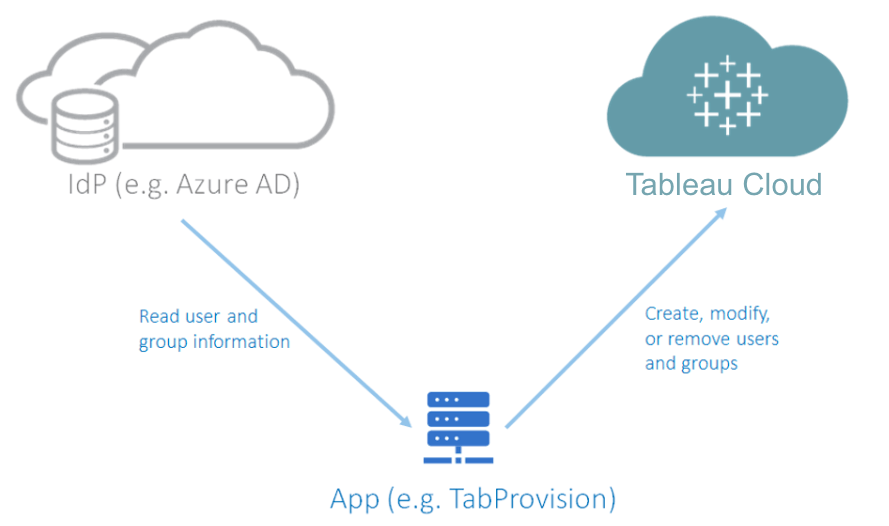
Build a custom app to automate provisioning with APIs
Alternatively, if you need more granular control over how user provisioning is performed for your organization, you can develop a custom app using the Tableau Cloud REST API. We have a ready-to-use, open-source application TabProvision to demonstrate how to automate the provisioning of users from your IdP to Tableau Cloud. The app reads the user and group information from the IdP, such as Azure AD, and automatically adds, modifies, or removes them on your Tableau Cloud site to keep them in sync with the IdP.
While this option requires more upfront setup, including developing the app and an environment to host it, it provides greater flexibility in configuration.
- The custom app gives you full control over how and when the user provisioning is performed.
- You can customize the user provisioning flow to accommodate any special processes in your organization.
- You can expand the custom app to read user and group information from multiple IdPs. For example, you may have internal users from Azure AD and external users managed separately using a different provider.
- It supports the grant license on the sign in feature (built into TabProvision).
- The same app can also provision users to on-premises Tableau Server with version 2020.3 or later.
Additional resources
To get started with automatic provisioning with Tableau Cloud and Azure Active Directory, visit the Tableau Help documentation.